Welcome to my Professional Space
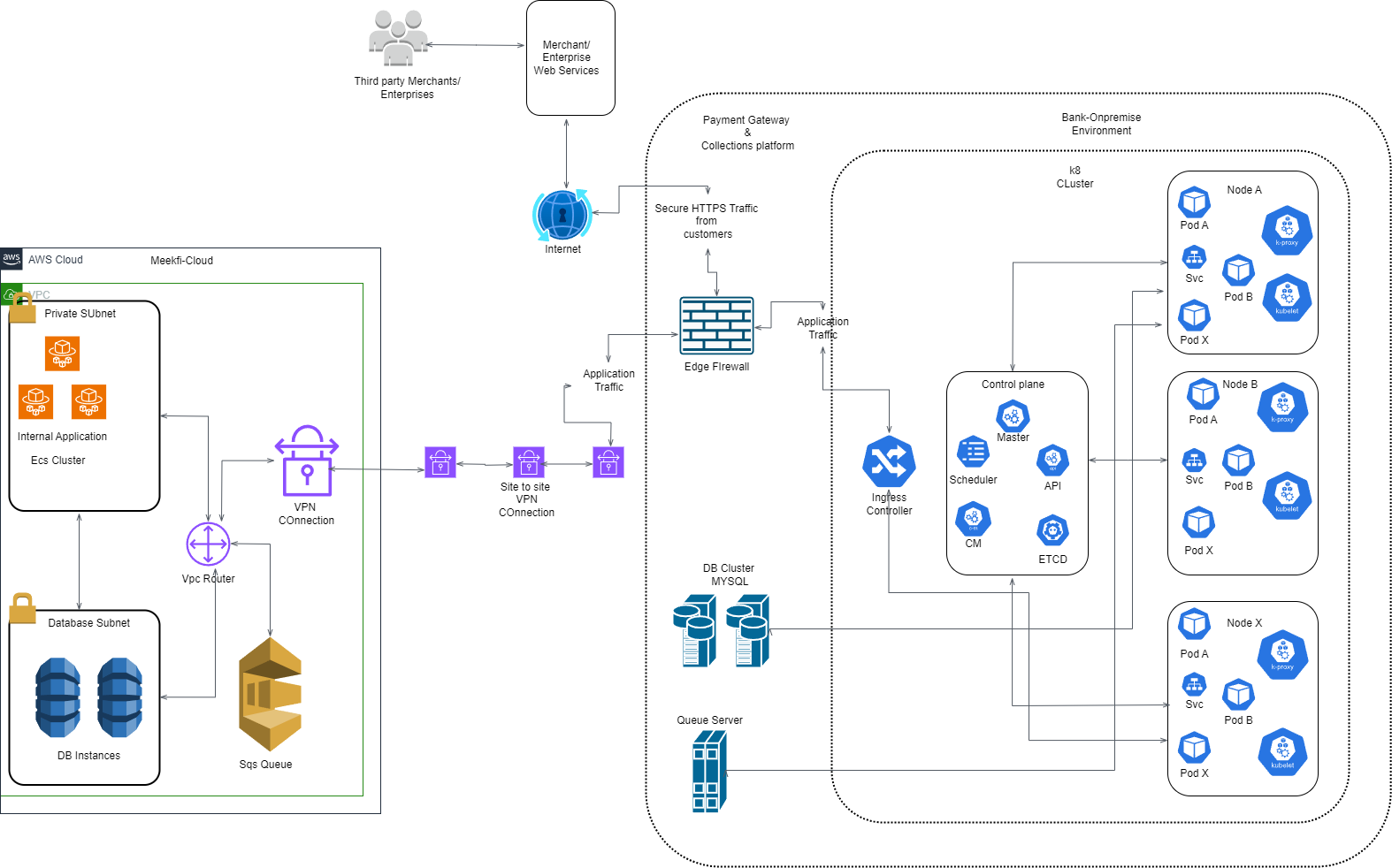
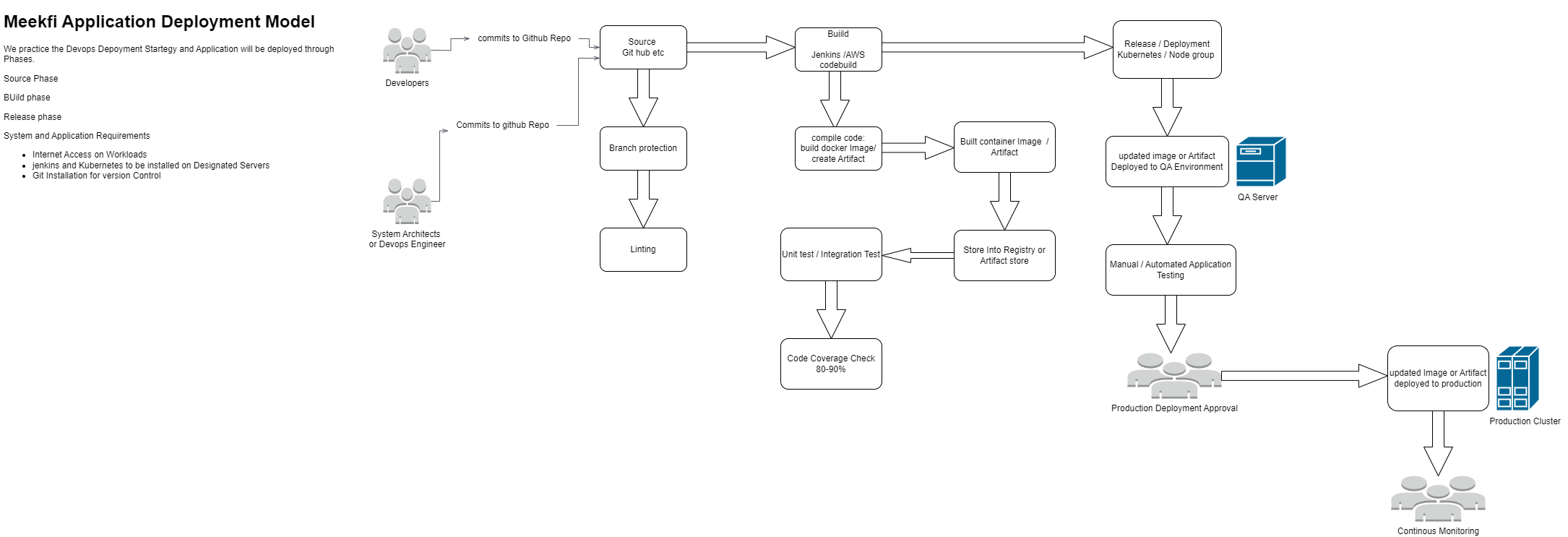
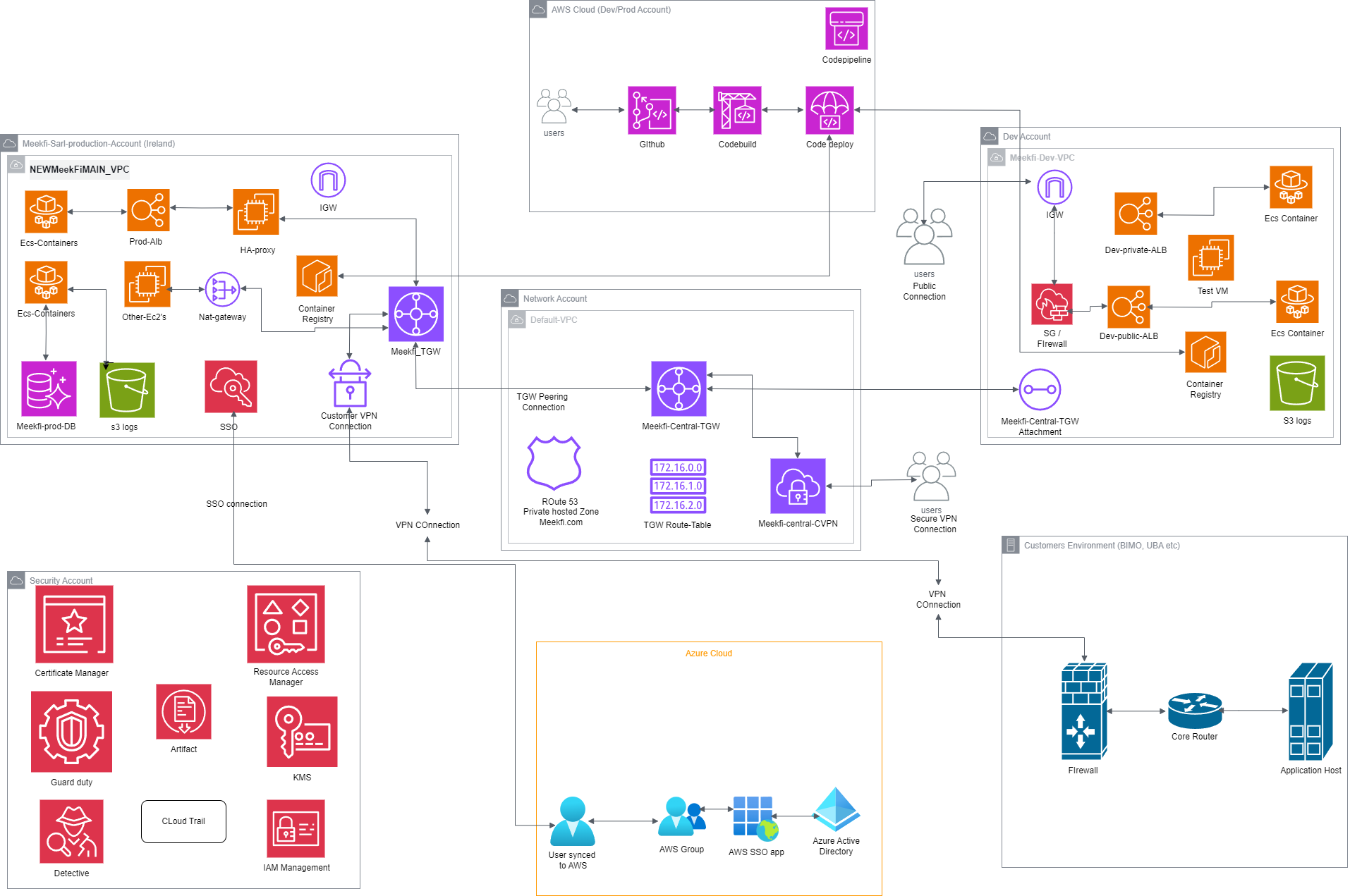
Hello, I’m Chuks, a dedicated Information Technology Architect with a comprehensive skill set in Cloud and DevOps Engineering, System Design, Web & Software Development, Cyber Security, Data Engineering, and IT Technical Consultancy. With a deep passion for technology and innovation, I specialize in creating scalable, secure, and efficient solutions that drive business success.
Throughout my career, I have successfully delivered cutting-edge projects that enhance operational efficiency, bolster security, and enable data-driven decision-making. My diverse expertise allows me to tackle complex challenges and implement robust systems tailored to meet the unique needs of each organization.
Explore my portfolio to see my work, learn more about my professional journey, and discover how my skills and experience can help you achieve your technology objectives.